Producing IPv6 traceroute results in HTML format using NMAP
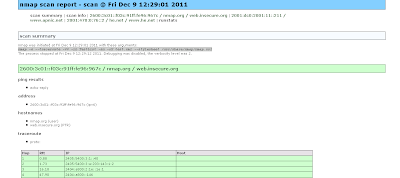
I searched how we can display the IPv6 trace-route results to web in automated manner. There may be different PHP / perl modules but using nmap trace route option we can archive similar fashion. we can have the list of hosts separated by space nmap.org www.apnic.net he.net we can use following command to create the XML output. nmap -6 --traceroute -vv -iL TestList -sn -oX test.xml --stylesheet /usr/share/nmap/nmap.xsl -6 to enable IPv6 -vv increase the verbosity of the oubput --sn no port scan -oX output XML --stylesheet where to find { to translate from XML to HTML } xsltproc test.xml --output test.html