l2tpv3 configuration reference
Reference Comparing , Designing and Deploying VPNs chap - 02 :
L2TPv3 is the enhanced version of L2TPv2 protocol. Mikrotik uses L2TPv2 i suppose but it offer another similar tunneling mechanism as EOIP.
L2TPv3 in cisco provides Pseudo-wire services to the customer. L2TPv3 only require the IP connectivity between peers but it can transport Ethernet, 802.1Q , HDLC, PPP framerelay etc.
Advantage over MPLS is the customer having the full control of their routing domain.
L2TP depolyment methods having 3 topologies
LAC - LNS , LNS - LNS , LAC - LAC
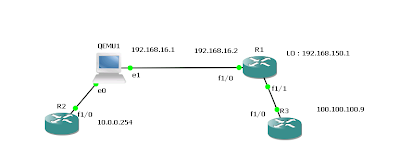
Following Diagram explain simple LAC - LAC L2TPv3 setup.
It uses two types of messages:
control connection messages - used for signaling between LCEs
session data messages - Used to transport layer 2 protocols and connections
Data channel Message Header having Session ID & cookie to correctly associate with the tunnel
Deploying dynamic Pseudowires session
1) configure CEF - Its default in IOSs now.
2) configure a loopback interface to use as the pseduowire endpoint ( need to have the connectivity)
3) configure an L2TP class ( optional)
L2TPv3 Class enables to configure number of control channel configurations.
authentication , keepalive intervals , receive window size, retransmission parameters, timeouts
4) configure a pseudowire class
5) bind attachment circuits to pseudowires
R1:
R2:
Between Two Circuits
CDP from remote devices :
Have to try the interoperability between cisco & mikrotik
L2TPv3 is the enhanced version of L2TPv2 protocol. Mikrotik uses L2TPv2 i suppose but it offer another similar tunneling mechanism as EOIP.
L2TPv3 in cisco provides Pseudo-wire services to the customer. L2TPv3 only require the IP connectivity between peers but it can transport Ethernet, 802.1Q , HDLC, PPP framerelay etc.
Advantage over MPLS is the customer having the full control of their routing domain.
L2TP depolyment methods having 3 topologies
LAC - LNS , LNS - LNS , LAC - LAC
Following Diagram explain simple LAC - LAC L2TPv3 setup.
It uses two types of messages:
control connection messages - used for signaling between LCEs
session data messages - Used to transport layer 2 protocols and connections
Data channel Message Header having Session ID & cookie to correctly associate with the tunnel
Deploying dynamic Pseudowires session
1) configure CEF - Its default in IOSs now.
2) configure a loopback interface to use as the pseduowire endpoint ( need to have the connectivity)
3) configure an L2TP class ( optional)
L2TPv3 Class enables to configure number of control channel configurations.
authentication , keepalive intervals , receive window size, retransmission parameters, timeouts
4) configure a pseudowire class
5) bind attachment circuits to pseudowires
R1:
l2tp-class digest_r1 digest secret 7 096F673A3A2A hash SHA1
pseudowire-class R1toR2 encapsulation l2tpv3 sequencing both protocol l2tpv3 digest_r1 ip local interface Loopback0xconnect peer-address VCID ( should be unique) pw-class [name]
interface FastEthernet1/0 no ip address duplex auto speed auto xconnect 172.16.0.2 100 pw-class R1toR2 sequencing both
R2:
l2tp-class digest_r2 digest secret 7 062526126F61 hash SHA1
pseudowire-class R2toR1 encapsulation l2tpv3 sequencing both protocol l2tpv3 digest_r2 ip local interface Loopback0
interface FastEthernet1/1 no ip address duplex auto speed auto xconnect 172.16.0.1 100 pw-class R2toR1 sequencing both
Between Two Circuits
R6#ping 192.168.20.2 size 1500 repeat 2 df-bit Type escape sequence to abort. Sending 2, 1500-byte ICMP Echos to 192.168.20.2, timeout is 2 seconds: Packet sent with the DF bit set !! Success rate is 100 percent (2/2), round-trip min/avg/max = 72/94/116 ms
CDP from remote devices :
R6#show cdp neighbors detail | inc Device|IP|Int Device ID: R1 IP address: 172.16.0.1 Interface: FastEthernet1/0, Port ID (outgoing port): FastEthernet1/0 Device ID: R7 IP address: 192.168.20.2 Interface: FastEthernet1/0, Port ID (outgoing port): FastEthernet1/0
R1#show l2tun session all
L2TP Session Information Total tunnels 1 sessions 1
Session id 56564 is up, tunnel id 23863
Remote session id is 61449, remote tunnel id 53859
Remotely initiated session
Call serial number is 10785
Remote tunnel name is R2
Internet address is 172.16.0.2
Local tunnel name is R1
Internet address is 172.16.0.1
IP protocol 115
Session is L2TP signaled
Session state is established, time since change 00:58:25
DF bit off, ToS reflect disabled, ToS value 0, TTL value 255
UDP checksums are disabled
FS cached header information:
encap size = 28 bytes
45000014 00000000 FF736353 AC100001
AC100002 0000F009 00000000
881 Packets sent, 881 received
744359 Bytes sent, 744061 received
Last clearing of counters never
Counters, ignoring last clear:
881 Packets sent, 881 received
744359 Bytes sent, 744061 received
Receive packets dropped:
out-of-order: 0
total: 0
Send packets dropped:
exceeded session MTU: 0
total: 0
Sequencing is on
Ns 872, Nr 872, 0 out of order packets received
Packets switched/dropped by secondary path: Tx 0, Rx 0
Conditional debugging is disabled
Unique ID is 1
Session Layer 2 circuit, type is Ethernet, name is FastEthernet1/0
Session vcid is 100
Circuit state is UP
Local circuit state is UP
Remote circuit state is UP
Have to try the interoperability between cisco & mikrotik


Comments